To follow-up on the outline posted in my SSL Overview posting, I will be digging into this process to break things down into a step-by-step approach.
Creating a certificate request isn't too difficult. So to get to the point, you need to launch the IIS MMC and connect to the server that is (or will be) hosting the site that needs the certificate...
1) Launch IIS as a domain administrator
2) Open the Default web site, and right-click properties
3) Select the Directory Security tab, and click “Server Certificate”
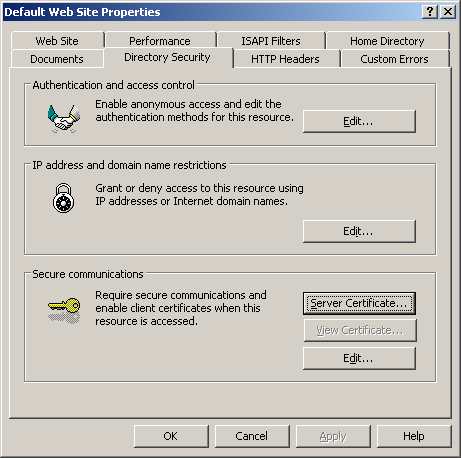
4) Select "Create a new certificate", click Next.
5) Select prepare the request now, but send it later. Click Next.
6) Choose identifying information (e.g. “Default Web Site”), bit-length 1024., Next. Again, enter more identifying information, click next.
7) The most important part of the certificate request is to choose the correct naming for the site.
- For instance, if this site is only going to be available internally, you can choose either the netbios name (e.g. servername) or full-DNS name (servername.domainname.local).
- If this site is going to be available externally, use the full external DNS name. (e.g. “intranet.domainname.com”)
8) Type more identifying information, click Next.
9) Choose the filename for the certificate request (c:\certreq.txt is fine). Click Next. Click Next. Click Finish.
That's all there is too it. The next step is to submit the request to a CA (Certification Authority), which I will cover is a follow-up post.